7 Costly IT Mistakes That Can Kill A Business
The cyclical pattern of life--and business--ensures that the deserving underdogs of yesterday get their chance to be at the cusp of glory today. Such is the case with the Information Technology field. The tipping point for IT, the moment that pushed it to the forefront of commerce, happened when technology became intricately weaved into the infrastructure of businesses. Over the past decade, its role has grown in leaps and bounds, widening its impact in the business world. What was once considered a vestigial presence in an organization has become the backbone of the entire digital ecosystem.

Now, an IT mishap stands to hit everything from a company’s reputation to its revenue. In this article, we will look at 10 critical IT mistakes that every company should be cautious of making, because a little slip-up in any of these areas can have an enormously detrimental effect on the life of your company.
Mistake #1: Not taking cybersecurity seriously
Consumers have always taken security seriously. When the world went digital, there was a long adjustment period before people felt comfortable with handing over their financial information to complete a shopping transaction online. This gave rise to things like SSL certificates, privacy policies and trust seals used as a visual cue to convey the security of a website or application. Now, in an age where personal data has become more valuable than gold, cybercriminals are using sophisticated tactics to identify and exploit weaknesses in IT infrastructures to get their hands on private data. Breaches, hacks and other cyber attacks have become commonplace and are costing companies more than 1.6 million dollars in financial damage.

Many small businesses think that cybersecurity is a problem of the elites. But research shows that smaller companies are increasingly becoming targets of these attacks because hackers know many of them don’t have the proper precautions in place to protect their IT assets. Research also shows that 60% of small business victims are at risk of going out of business within 6 months of suffering a cyber attack.
With such an attack, the impact is three-fold: revenue lost during the event of the attack, revenue lost cleaning up the damage, and an indirect loss in revenue as a result of a tarnished credibility and reputation.
Mistake #2: Obsessively sticking with legacy systems
It doesn’t always take years for technology to become obsolete. Sometimes it happens in months.
Many companies are still using antiquated software, processes and other technology to run critical business operations. There are several reasons for this, the main one being legacy systems--often homegrown--are customized and enhanced to a point where the thought of replacing them may seem like a gargantuan task. While they might be able to handle critical functions, however poorly, legacy systems tend to do more harm than good. Not only do they stop receiving updates and security patches from developers, but they are also very unreliable.
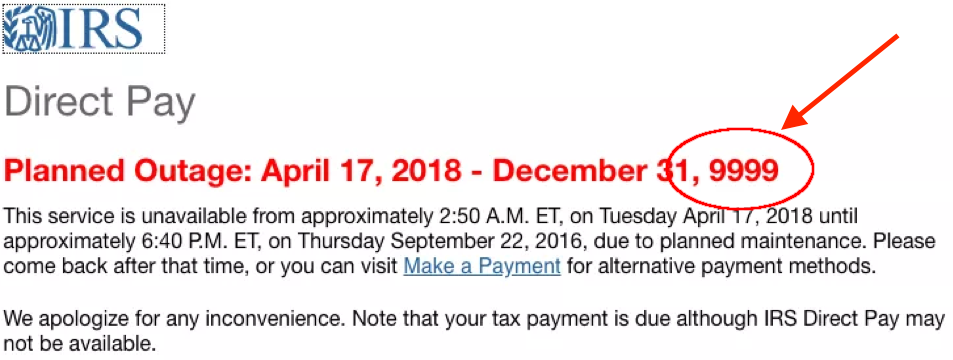
For example, during 2018 Tax Day, millions of last-minute tax return filers rushed to the IRS website, causing it to crash. While the reason for the outage could have been anything, it is worth noting that the IRS runs on outdated IT infrastructure (two of the systems are almost six decades old!) which puts it at a higher risk for failures.
Maintaining and supporting a legacy infrastructure can take a hefty amount of money that could be better spent elsewhere. It can also limit opportunities for innovation and efficiency that newer technology allows. A research report by Vanson Bourne shows that businesses stand to reduce their operating costs by up to 13% on average by modernizing IT systems, and they also gain the potential to boost their revenue by over 14% ($1 billion) a year.
Mistake #3: Not prioritizing scalability right from the get-go
One of the most defining features of strong enterprise software is its scalability. When it comes to software, scalability refers to its ability to seamlessly handle an increased workload.
An unscalable system is like a house with a very weak foundation. It will start to come apart the moment the stress load exceeds its capacity.
In an attempt to cut costs, many businesses prioritize budget over scalability very early on. At first, this may not seem like a big deal because the demand on the application architecture at the beginning is usually light. But as usage increases, so will the problems. Updating apps with patches may alleviate these problems to a certain extent but they also increase complexity and make it difficult to spot future problems, thereby increasing the risk for poor performance, such as slow loading times.

Ensuring that the software your company uses (or is built upon) is vertically and horizontally scalable and easily modifiable in terms of usage, data storage capacity, and coding right from the start will prevent your enterprise from getting stuck with a rigid software that hinders--rather than celebrates--growth.
Mistake #4: Not testing your disaster recovery plan
A reliable disaster recovery plan is imperative to ensure that when things go awry, your operations won’t go defunct. Tech--like humans--is mortal, and sometimes the most seemingly innocuous elements can cause disastrous business outcomes. Most companies know this and are taking disaster recovery seriously, but having a plan doesn’t automatically mean that it will work. In fact, in a report by Spiceworks that surveyed 762 IT professionals working across businesses throughout North America and Europe, 95% of the respondents stated that their company had a DR plan, but 23% (one in four) of them had never actually tested it to see if it worked. Moreover, 30% of the respondents reported losing revenue due to a service outage.

Relying on an untested DR plan is a recipe for expensive disaster waiting to happen, because you are blindly putting your faith in a system whose operability hasn’t been proven. But, here’s another problem--consistency. A fraction of businesses do test their back-up plans, but not often enough.
Regular testing is critical to identify flaws in plans so that they can be improved and bolstered over time. This way when a catastrophe strikes and causes a power outage, hardware/software failure or network connectivity problems, your critical moving parts will not stop working, and your operations will receive little to no disruption.
Mistake #5: Not taking insider threats seriously
Thanks to movies and TV shows, when most people think of cybercrimes they think of outsider threats--a group of hooded folks in a foreign country coding away at something sinister. But the real enemies might be situated a lot closer to home.

For example, take the case of Jason Needham. He was an engineer who worked for Allen & Hoshall, a Tennessee based Engineering firm. In 2013, he parted ways with the firm to start his own company, HNA, but he still had one foot discreetly planted in his previous employer’s territory. For two years after his departure, he continued accessing the file server of his former employer, sealing critical information like staff emails, project proposals, marketing, and budget documents. When asked about it in court, Needham tried proving his innocence by claiming that he was just checking the old system purely out of habit and that there was no criminal intent behind it. The veracity of this claim was questioned when a client of Allen & Hoshall received an unsolicited proposal from Needham that looked strikingly similar to the one used by the firm.
Along with losing his engineering license, Needham was sentenced to 18 months in prison.
Businesses have historically focused on protecting the perimeter of their organization’s kingdom from outside attacks, but over half of all breaches stem from intentional or unintentional plunder from someone on the inside, like a disgruntled employee, an uninformed employee or a third party contractor with access to critical systems. These types of breaches, unfortunately, cause the harshest of financial damage, and they are also the most difficult to detect. A research report by Ponemon Institute puts the average cost of insider-related incidents at $8.76 million.
Mistake #5: Not being cautious when using Open Source Software

Open source software gives users the ability to freely access, modify or distribute the source code as they please, and it is used by many tech giants like Google (for Chrome and Android), IBM, and Amazon (AWS). There are many benefits contributing to the popularity of the Open Source platform. One is that it enables developers to use pre-written codes as the building blocks of their own software. Along with that, there is no upfront cost involved with downloading a code from an open source. Open Source Software is also quite reliable since they’re constantly being improved by thousands of developers all over the world. This means if someone notices a bug, it will be fixed fast. Another benefit is their longevity. The software’s life isn’t dependent on its parent company’s ability to stay in business and support it with important patches.
The prevalence of Open Source Software has essentially eliminated the need to ‘reinvent the wheel’ by creating an app or software from scratch. But it does have its costly drawbacks that many ignore. In 2003, Cisco acquired the networking hardware brand Linksys for $500 Million. It was later found that Linksys was using Open Source Software that violated the open source licensing requirements, something Cisco wasn’t aware of at the time of the acquisition.
Cisco was hit with a lawsuit by the Free Software Foundation (FSF) for breaching a General Public License requirement which states that anyone who redistributes a program based under that license is required to make the source code of the program available to its recipient (in this case, Cisco’s customers).
Businesses working with any software, be it Open Source or Closed Source software, must make it a priority to check and abide by the license requirements. Open Source Software usually comes with licenses, such as Apache, MIT, GPL, AGPL and more. All of them have different requirements, some being more permissive than others.
Mistake #6: Blind overreliance on offshoring
There are many reasons why businesses choose to offshore their IT operations, one being that it’s a less expensive way to achieve big dreams. But offshoring has a dark side that’s conveniently hidden beneath that mask of affordability.
Appster, a multi-million dollar app development agency based out of Australia, underwent voluntary liquidation in 2018. It seemed to have a promising future, with the potential to reach the ranks of Apple. The company was started on a shoestring budget of $3000 and was making over $19 million dollars in revenue in just 7 years. But its downward trajectory from riches to ruins happened fast--in just four months--and offshoring was one of the reasons behind this grim outcome.
Since the company started on a humble budget, it's understandable why offshoring app development might have seemed enticing for its creators, but even after the firm attained significant growth it still chose to offshore development which--prioritizing growth over stability--ultimately made them lose control. In short, the quality of apps sucked and the undeterred obsession with growth meant they were inundated with orders without having the necessary processes in place to meet those demands.
Seeking cheap labor isn’t always a good idea because chances are, something will have to give...and most likely, it will be quality. Along with that, you will have to sacrifice control in those facets of the operations you decide to offshore. This can arise from low transparency, lack of accountability, and problems due to communication and cultural barriers.
Mistake #7: Letting Production Outages Go Undetected

Outages in a business’s production website or APIs are notoriously difficult to
detect. Most problems do not present themselves in ways that system monitoring
products on the market today are able to discover, as most production outages
are specific to product features unique to that business.
In order to detect these complex issues, engineering teams are forced to create
complex, ad-hoc testing systems which are difficult to maintain and pull
development resources away from business critical feature development.
One way to keep your engineering team on-task and still ensure your production systems
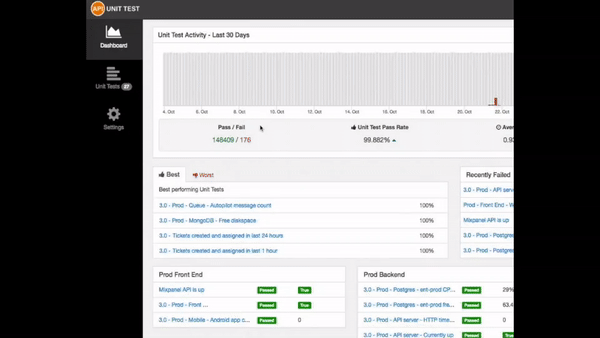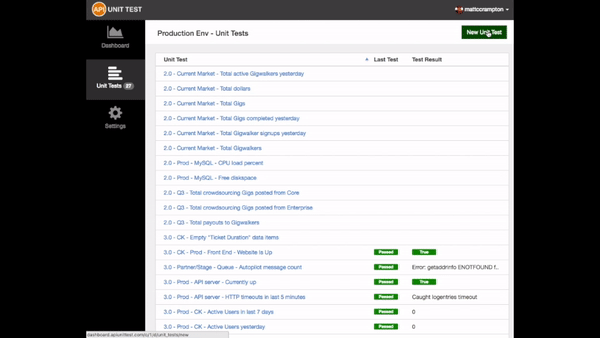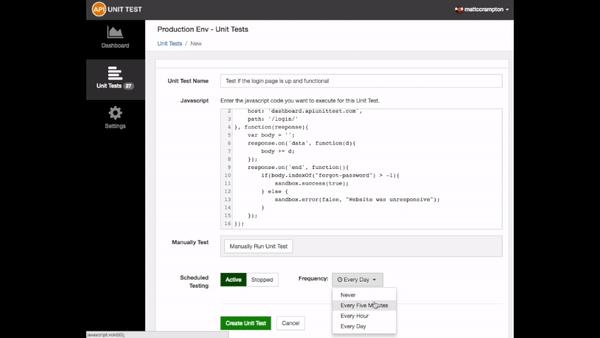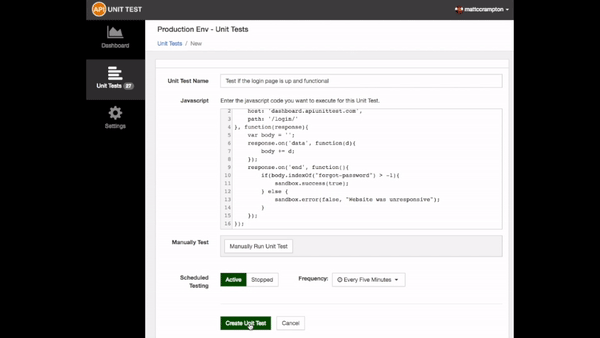
are being monitored is to utilize a platform like API Canary
API Canary is a production testing platform that allows developers and dev ops
engineers to build and deploy custom production tests that go beyond the
standardized testing tools available on the market today and directly test the
business specific pieces of a company’s infrastructure that matter most.
These production tests are deployed and executed, on a schedule, using our
custom, multi-cloud, serverless platform, eliminating the need for the complex
home-grown systems in use today.
As production tests are executed, results are instantly reporting via our
analytics dashboard and, if necessary, pushed to alerting mechanisms such as
Twilio and PagerDuty.
Production tests, written in Node.js, are created via API Canary’s
web based code editor or pushed into the platform directly via our APIs using the
same Continuous Deployment workflows teams already use to integrate with
platforms like Heroku or Circle CI.
These production tests can be configured to execute, on a schedule, in one or
more of the dozens of datacenters our multi-cloud, serverless platform
supports.
API Canary connects directly with the tools that engineering teams already use
to escalate errors such as Twilio, PagerDuty, and Slack so that any test
failures can immediately be addressed.
Parting Thoughts
There have been thousands of victims with thousands of harrowing stories for
each of the mistakes mentioned above. But, there is a whole lot of truth in the
old adage: knowledge is power. By knowing the most common IT mistakes that hold
the potential to cause drastic damage to the best of the best, you can ensure
that your app, software or business’s IT infrastructure will never have to
suffer for being unprepared.